There isn't a promise that even with the most beneficial safeguards some of these matters is not going to occur to you, but you'll find methods you usually takes to reduce the possibilities.
A clear data governance tactic as well as discoverability and transparency capabilities expedites finding, processing, defending and securing data and makes the procedure much more scalable To maximise and monetize data sources.
They even have no more functions, bad customer guidance, and might be pretty aggravating within their try and upsell you on the compensated Edition.
Security engineers. These IT specialists secure business assets from threats having a deal with excellent Handle in the IT infrastructure.
Challenges contain making sure all components of cybersecurity are continuously current to protect in opposition to opportunity vulnerabilities. This can be Primarily tough for smaller businesses that do not have suitable employees or in-property means.
Malware infection: Malware is among the more frequent strategies to infiltrate or problems your computer via Laptop or computer viruses, worms, Trojan horses, spy ware, and adware. These viruses are often utilized to intimidate you with scareware, which is usually a pop-up information that informs you your Laptop or computer has a security problem or other false details.
Use powerful passwords. Choose passwords that may be hard for attackers to guess, and use various passwords for different applications and devices. It's best to employ long, strong passphrases or passwords that encompass not less than sixteen characters. (Choosing and Preserving Passwords.)
See far more Boost alter detection, identify data variations swiftly and proactively prevent problems from threats and human mistakes.
The particular results in of profits leakage will depend upon personal situations. Your company's opportunity vulnerabilities might be exceptional to your situation and composition. As a result, you'll need to review your operations to establish spots where you can tighten Cheap security up.
Review the plan each year or when alterations to rules and polices warrant changes to help keep the policy related and compliant.
A successful cybersecurity posture has multiple levels of protection spread through the pcs, networks, packages, or data that a single intends to keep Secure. In a company, a unified menace administration gateway method can automate integrations across products and solutions and accelerate important security operations functions: detection, investigation, and remediation.
An effective cybersecurity strategy can offer a robust security posture towards destructive assaults created to access, change, delete, wipe out or extort an organization's or person's programs and sensitive data.
Utilizing artificial intelligence (AI) and equipment Studying in spots with higher-volume data streams can help enhance cybersecurity in the following three main types:
By flooding the concentrate on with messages, connection requests or packets, DDoS assaults can gradual the system or crash it, stopping legit traffic from utilizing it.
 Ariana Richards Then & Now!
Ariana Richards Then & Now! Richard "Little Hercules" Sandrak Then & Now!
Richard "Little Hercules" Sandrak Then & Now! Barbi Benton Then & Now!
Barbi Benton Then & Now!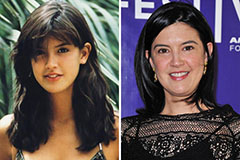 Phoebe Cates Then & Now!
Phoebe Cates Then & Now! Lacey Chabert Then & Now!
Lacey Chabert Then & Now!